What is BeSECURE™ and Who Should Use it?
BeSECURE™ is a vulnerability assessment and management tool that uses patented technology to accurately identify vulnerabilities and threat intelligence to prioritize them by risk.
Organizations of any size, from 100 to 10,000 use BeSECURE™. Vulnerability management is a necessity for any industry, but especially those with cybersecurity compliance and regulatory standards. IT security, banking and financial institutions, infrastructure, public sector, and government all require vulnerability management as part of a layered cybersecurity strategy to ensure private, sensitive data is protected and business critical systems are secured.
BeSECURE™ supports a wide range of compatible systems, including Microsoft, UNIX, Novell, network devices, and others. It is quick and easy to stand up, so your team can go from installation to active scanning in minutes. Additionally, our top-rated customer support team helps ensure any questions you have are answered quickly and thoroughly. If you’d like to learn more about how BeSECURE™ can optimize your security efforts, contact our expert consultants.
How to Use BeSECURE™
BeSECURE™ was designed with easy-of-use and flexibility in the forefront. In less than 5 minutes of booting up, networks are capable of being scanned. Deployment modes cover cloud-based, on-premise, and even a hybrid model between the two. Capable of scaling, it’s a cost-effective scanner that’s great for PCI compliance. It delivers automatic, accurate scanning to stay ahead of the latest vulnerability threats.
Reports and results are displayed within an intuitive, easy-to-understand console with robust filtering capabilities. This ensures your team always has a clear picture of your network’s current security posture and can easily share that information with stakeholders.
Quickly pinpoint which weaknesses are the most exploitable, enabling you to focus on high-priority vulnerabilities and avoid chasing lower-risk vulnerabilities and false positives.
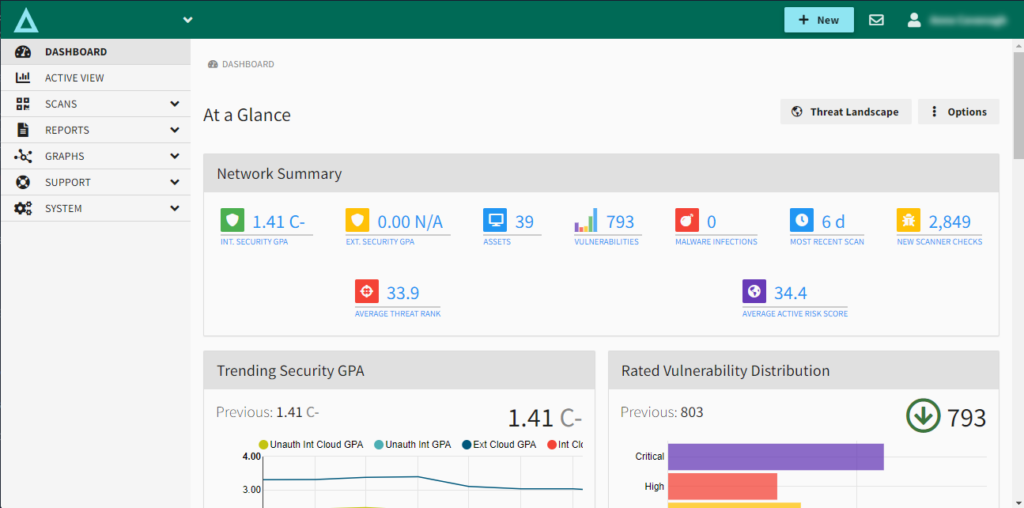
BeSECURE screenshot from an interactive demo displaying dashboard of At a Glance view
Get a 5 Minute Guided Tour of BeSECURE
Take a guided tour of BeSECURE and see some of the impressive vulnerability management features.
BeSECURE Features
Quick Scan gets testing started in minutes:
- Scan for PCI, CIS benchmarks, HIPAA, SOX and other compliances in one solution
- Scans local and global network ranges
- Distributed scanning architecture for large networks with enterprise-wide scans
- Scan Profiles can check large networks quickly for a small subset of problems
Automated reporting and updates of threat database
- Differential reporting highlights newly added IPs, ports and services
- Powerful search engine to quickly filter and search reported vulnerabilities
- Segment reports into locations, IT teams, locations, and more
- Specialized, customized, and consolidated reports available
Accurate and efficient vulnerability scanning
- Correlates data on dynamic assets
- Connects and integrates with other enterprise-level systems and tools
- Creates efficiencies by being simple to deploy, learn, and maintain
Resource friendly, fully supported
- Non-intrusive and consumes minimal bandwidth
- 24/7 unlimited phone support with access to Beyond Security experts
BeSECURE Vulnerability Management/Assessment Use Cases
Need to Meet PCI Compliance
BeSECURE is a certified ASV PCI Compliance regulations and standards scanner and meets the reporting requirements for government, financial, and medical industry security standards. BeSECURE can scale from single domain PCI scanning to international network scanning that includes hundreds of thousands of IP addresses.
Need to Complete a Vulnerability Assessment Audit
Utilizing a vulnerability assessment scanner in-between compliance and regulation standard audits helps speed up the process. BeSECURE’s dynamic reporting keeps track of exploitable weaknesses and remediation efforts to fix them. Reports can be customized and specifically filtered to include compliance standards that are met before the audit deadline.
Find Known CVE’s, Prioritize by Risk Context
Endless vulnerabilities are impossible to try to remediate. Threat intelligence and machine learning help apply risk context, prioritizing vulnerabilities based on an organization’s unique network environment. These measures ensure the highest priority threats stay in focus instead of spending limited time and resources on vulnerabilities that may not be true threats.
See More of BeSECURE
Get a closer look at how BeSECURE can help your organization with vulnerability management and assessment.
